Vinod Kumar
Enpass team member-
Posts
509 -
Joined
-
Days Won
42
Everything posted by Vinod Kumar
-
Hi @Lox_ There is something odd in lsof output. All three process firefox, chrome-gn and gjs are connceted with Enpass with same peer port (36776) and FD. Peer ports should be different like localhost:~$ lsof -i:10391 COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME firefox 3140 vinod 110u IPv4 56432 0t0 TCP localhost:48872->localhost:10391 (ESTABLISHED) chrome 3572 vinod 260u IPv4 54522 0t0 TCP localhost:48858->localhost:10391 (ESTABLISHED) Enpass 4289 vinod 40u IPv4 53849 0t0 TCP *:10391 (LISTEN) Enpass 4289 vinod 43u IPv4 55788 0t0 TCP localhost:10391->localhost:48858 (ESTABLISHED) Enpass 4289 vinod 55u IPv4 55825 0t0 TCP localhost:10391->localhost:48872 (ESTABLISHED) What is this process gjs and why it is connecting to Enpass?
-
Hi @Lox_, We tried to reproduce this issue with a fresh virtual machine for Ubuntu 18.10 with default configurations. All browser extension are working fine. There must be something we are missing here. How an extension connects with Enpass is not radically different from version 5. Enpass runs a websocket server on 127.0.0.1 on one of the port (10391 - 10395). An extension tries to connect to one of these port, if it couldn't find the server or Enpass couldn't determine connecting browser pid it fails. Please share following details: 1. Output of `lsof -i:10391` 2. Are you using any proxy? If yes, please set it to ignore 127.0.0.1. Also, adjust any firewall rule accordingly. 3. Are multiple instance of Enpass running in different userspace (a multiuser system)? 4. Chrome and Firefox version and source of installation (ubuntu repo, snap or flatpack) Your time and effort are greatly appreciated.
-
Hi @Alex Gurenko, Goto Settings->Browser->Review Browsers. If you find any rejected browser there, just remove it and extension should work fine.
-
Hi @itsuia, Can you share more info about your webdav server software? It will help us to recreate similar webdav environment for testing. Cheers
-
UI broken on HiDPI displays in v6 [NOT SOLVED]
Vinod Kumar replied to ShikiByakko's topic in Windows PC
Hi @ShikiByakko, Non integer scale factors i.e. 1.5 (150%), 1.25(125%) are not playing well with Chinese and Japanese. Though official Qt (GUI toolkit for Enpass) doesn't support non integer scaling, we did applied a patch to support it. We will be disabling it for selected languages in next update. Thanks for update. -
Hi @apollo13, You didn't noticed the change in sha algorithm in @Anshu kumar 's reply. It is sha512 not sha256. Yes, master password is UTF-8 encoded. Cheers,
-
Hi @Tadly, Thanks for maintaining arch packages. Its under a different package name `enpass-beta`. Also it is available in the stable channel (rather than testing where v5 betas are published). It will be installed as a separate app, without breaking existing v5 installation. Cheers.
-
Hi @Psi-Jack, You can find more details about security and cryptography in Enpass here: https://www.enpass.io/security/ https://www.enpass.io/docs/enpass-security-whitepaper/index.html libsodium is being used for encrypting browser extension communication channel. It is present in /opt/Enpass/lib folder that's why running ldd on Enpass binary says libsodium.so.18 => not found which just means that ldd couldn't find the library in your system at standard locations.
-
Hi @Sam, Let me have this opportunity to assure you that there is such no backdoor in the algorithm. There is clearly some misunderstanding here. Let us find out the probability of having at least two consecutive digits in a number of various length using a computer program P(length 2) = 10 / 100 = 0.1 P(length 3) = 190 / 1000 = 0.19 P(length 4) = 2710 / 10000 ≈ 0.27 P(length 5) = 34390 / 100000 ≈ 0.34 P(length 6) = 409510 / 1000000 ≈ 0.40 P(length 7) = 4685590 / 10000000 ≈ 0.46 So, as length increases probability increases. and is approximately P ≈ (∑k - ∑(k-n+1))/k^2 where k >= n k is sample space of single digit n is length of password In our case k=10 and n=10 P(length 10) = (55 - 1)/100 = 0.54 So, Probability of occurrence of at least two consecutive digits in a random password of length 10, using only digits is 0.54 i.e. 54%. And it is very close to your statistical calculation. Cheers:)
-
Hi @Sam, Welcome to Enpass. Can you please elaborate the problem in more detail so that I can address your concerns? Do you mean to say "Measure of occurrence of consecutive number pairs in a random password of length 10, using only digits"? Regards, Vinod
-
Hi @Arthur Rump, Windows Hello dialogue is supposed to be used with Store apps only. There is an user interface issue in Windows Hello dialogue when used in Win32 apps. We are in talk with Microsoft Hello team regarding it but there is no apparent fix soon.
-
After import from 1Password, Enpass brings up multiple passwords for one entry
Vinod Kumar replied to Jay's topic in Mac
Hi @Jay, Thanks for detailed information you provided. This is the first time we are getting this type of complaint. It seems related to webforms save by a older version of 1Password. While we are looking into reproducing and fixing the same, you can use 1Password import from CSV. It will not contain any form fields and will require less manual work afterwards in your case. Cheers, -
Hi, This is the bug in Gnome/GTK+3 native file chooser dialogue in linux. https://bugzilla.gnome.org/show_bug.cgi?id=787128 As of now you can type you network location manually. Open file manager -> navigate to desired folder -> press Ctrl+L -> copy path of folder from location bar. Repeat the same with file chooser dialogue in Enpass. Press Ctrl+L -> paste in location bar. Cheers
-
Hi @nasko, Nothing wrong with Enpass here. It is due to the fact TPM is not in secure state because of this vulnerability. https://go.microsoft.com/fwlink/?linkid=852572 Microsoft is yet to release a firmware update to fix this issue. Enpass should work as intended after the firmware update. Thanks
-
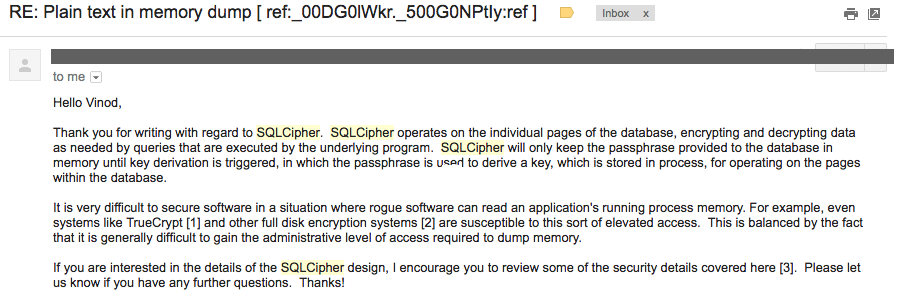
Hi @MatMaul There is nothing like annoying in your queries. This is the purpose of discussion forums and we really appreciate your presence here. And many thanks for choosing Enpass and showing your trust. Security is an ongoing process and you shall definitely see improvements in next major release. Let me attach here the answer from SQLCipher author himself. It should make things clear.
-
Enpass Desktop causing wireless network issues on Windows 10 14393
Vinod Kumar replied to Kevin Fulton's topic in Windows PC
Hi @rauppe31, This issue is related to the Qt framework bug which has not been resolved yet. We tried to hardcode the environment variable, but it keeps on causing sync related issues on some of our test systems. We prefer to wait until the upstream bug has been fixed. However, next major release, Enpass 6 will not use Qt network APIs and will not have this bug. We are sorry that you have to live with manual workaround for a while. -
Hi @fmfm, Enpass uses SQLCipher (open-source and peer-reviewed cryptography engine) with 24000 rounds of PBKDF2-HMAC-SHA1. In context of PBKDF2 or HMAC, SHA1 is still quite suitable from a security standpoint. We have already increased the number of iterations with improved algorithm, and we will implement these changes in production stream from next major release 6. And finally as concluded in their post https://blog.elcomsoft.com/2017/08/attacking-the-1password-master-password-follow-up/ , choice of strong master password is the most important factor guarding your data. Cheers
-
Hi @vsq, You won't be able to run Enpass without pulse audio installed. We don't have a command line flag for disabling it. Though this library is installed by default with almost every Linux desktop system, but you have a unique situation here. Please install relevant pulseaudio package on the target system and try again. Cheers
-
Hello Andre! Thank you for reporting the vulnerability and co-operating with us throughout the fixing process. Well, the vulnerability has been fixed and the updated version 5.5.3 has been rolled out on June 12, 2017. More details here- https://www.enpass.io/blog/an-update-on-the-reported-vulnerability-of-enpass-for-android/ Also, it's a request to every Enpassian who's using the version 5.4.6 to 5.5.2 in Android to please update the app to the latest version 5.5.3 immediately. Cheers!
-
Hi @lucas , Can't provide an ETA. The library shouldn't create a problem as webdav specs are not changed after its depreciation. The problem can be due to many other reasons including server implementation of Webdav. Please try webdav sync in desktop version of Enpass. Also if possible, can you provide us a demo account?
-
Hi @Arthur Rump, Thanks for providing really helpful pointers. We will be including Windows Hello support in next major version.
-
Hi @lucas, Yes, we are moving to another webdav implementation (c++ libcurl based) in next major version.
-
Hi @lucas, I think you are pointing towards the recent SHA-1 collision attack. PBKDF2 in SQLCipher use HMAC-SHA1 and it is still secure. Both are not quite the same thing.
-
Hi @ctrl_alt_pasta, What @Ivarson said is certainly right. Enpass doesn't do any security validation for you. Your browser is equipped with the best tools to do any security validations about identity of host. Constant updates are provided to guard against spoofing attacks like address bar spoofing. So, one should always pay attention to browser address bar warnings for broken or invalid certificates. However before autofilling, Enpass always match the domain name for saved items and shows only relevant items. This protects you against phishing attacks with look-alike domains.
-
Sqlcipher has api 'PRAGMA kdf_iter' to configure number of iterations for needed.