Search the Community
Showing results for tags 'security'.
-
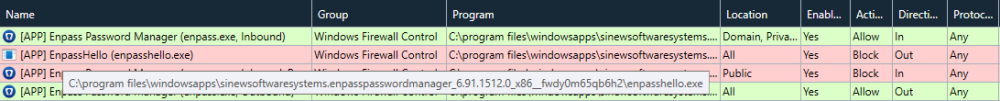
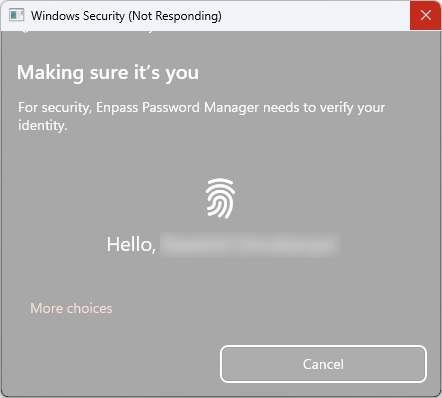
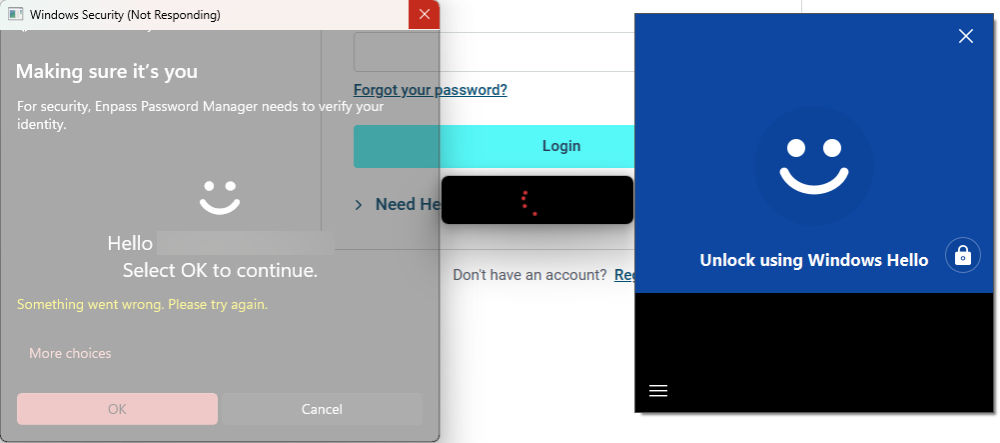
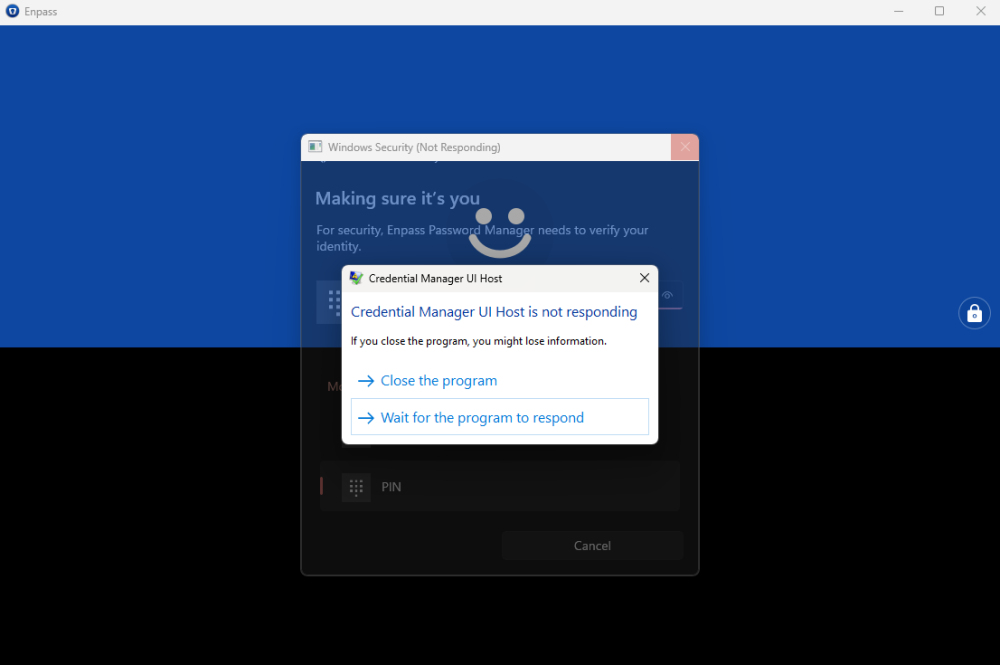
Hi all, As the title states, I've long been having this random issue with Enpass's Windows Hello Security dialog randomly freezing for 5+ minutes on my 32GB RAM i7 Surface Pro 7+ whenever I attempt unlocking it: After the freezing, it just shows an error message that "Something went wrong. Please try again." (as can be seen in the second image) and requires me to reauthenticate with Windows Hello yet again. Upon reattempting to authenticate with Windows Hello, it still freezes for another 5+ minutes! Only way to gain back access to my credentials is to cancel the Windwos Hello security dialog (which sometimes also takes another 5+ minutes after clicking the Cancel button) and enter my master password manually. However, to make matters worse, sometimes even clicking the Cancle button doesn't help, as after the 5+ minutes wating for it to Cancel, the moment I click the manual password entry text box in the Enpass main window, it yet again prompts for Windows Hello authentication. This has been a serious productivity-hampering bug that keeps randomly occurring in Enpass for the past several versions, and it still persists in Enpass v6.9.1 (1512) which I currently have installed from the Microsoft Store. What's going on? Also, I earlier noticed that the Enpass Windows Hello was attempting to connect to the internet for some reason, what's that for? Could it be because I blocked it from the internet that these random freezes are occuring?
-
The Forum is floated by spam messages. If Enpass is not able to add proper spam detection to their forums or at least human supervision that reacts in a time frame distinctly under 24 hours – why should potential customers trust Enpass security if the public representation to user seeking for support is so bad?
-
As i have been using enpass for past several months i even got to know about enpass key file to enhance vault security but there are still few concerns which i am about to share. 1: for security new users do not know about enpass key and once a new user have created primary vault then it is almost not possible for them to move to another vault and keep primary vault without enpass key. There is no option to set or change default primary vault if i want to. 2: Even if you have created primary vault with enpass key it can be hacked very easily. Enpass Database + keyfile is located on same system once a hacker got into your pc using RAT which is very common scenario they can access your all files in drive and using key logger they can capture your password for enpass. So when a hacker have access to a pc having enpass keyfile does not make it secure. I am a security researcher and i know what i am talking about. Now a days malware have became so intelligent they can be asked to find specific file on that computer or even on that network and once they find name of extension matching file it can be uploaded to hacker's server. having 2FA on Authy or Google Authenticator or which ever you use is much more reliable way to add an extra layer of security to your enpass vault. Why don't we put a 2FA by default for primary vault? Even if it is protected by key file on new device vault must ask for 2FA code? It can be implemented and user gets to choose if they want keyfile and 2FA both activated or only key file or only 2FA. I have tested the scenario (2) explained above using my personal computers and i was able to access it very easily. It is my humble request to add this 2FA including keyfile to make enpass more secure and a single keyfile and a password is not enough to secure it. even if we keep keyfile on a USB drive our vault needs it and when we will connect our USB to that pc for vault unlocking it can be accessed by hackers like all other normal drives. Also please add feature to change primary vault if someone creates a new vault with keyfile or how ever there must be an option to change primary vault. I hope i am not missing anything and was able to explain it clearly but if i am missing something please do let me know.
-
My bank has started using 'Verified by Visa' (VbV) as an additional security measure. A different password is required for each financial organisation using VbV. As a workaround, I have created a separate record in Enpass, titled 'Verified by Visa - [bankname]'. I have then generated a password specific to VbV and [bankname] within that record. Ideally, I would be able to generate a bank login password and a separate VbV password in two separate fields, within the same Enpass record. In general, there may be other reasons for having more than one password generated for a given Enpass record or organisation. Please amend Enpass to allow this.
- 1 reply
-
- verification
- banking
-
(and 1 more)
Tagged with:
-
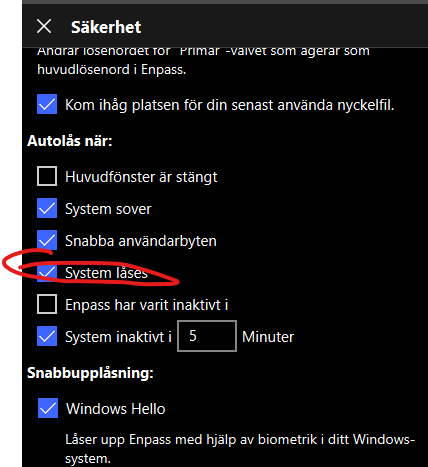
There seems to be a glitch in Enpass, where it doesn't lock during System Lock (Win-key + L) even it the setting is applied as shown below. The bug occurs (for me) only if I initially unlock Enpass through the Helper Window in System tray. If I initially unlock via the main Windows, the "System lock" works as expected. Enpass 6.7.4 (934) Windows 11 21H2 Fulltime Windows Hello-activated
-
Hello! I would like to know if there is an 2FA-Option additionally to the Master-Password when I open my Passwortmanager? Of course I hope, that nobody cracks my Master-Password. However "better safe than sorry" ... since 2FA is an important security-feature, I wonder why this option to add an 2FA (and I don't mean the Logins for my inside-Password) is not available yet? Or did I miss it? Thanks for your answer in advance. Best Regards
- 2 replies
-
- authentication
- two-factor
- (and 3 more)
-
Maybe you read the headlines: There was a massive iPhone hack. A Google team has found that thousands of iPhones were hacked - just by visiting a infected website. This allowed the attackers comprehensive access to the data in the iPhone: WhatsApp, Signal, SMS, gps-location, photos, contacts and - yes - even the keychain with the passwords should have been open. An incredible Bug! My question: Was Enpass also affected? Could attackers - even theoretically - read the passwords from the Enpass database? As far as I know, Enpass uses the iOS keychain to store the masterpassword, if you use biometric unlock. Who knows more?
-
Hello, I am relatively new to Enpass, I noticed, that after reboot, I can use the PIN to access my fault. How can this be secure? This means that the Masterpassword is stored locally on the flash memory. This and the fact, that there have never been an security audit for iOS really worries me. Can someone explain to me, how this might possibly secure? I have a feeling, that the reason, why there is no security audit is, that they know, that there is no way there application passes the audit.
- 18 replies
-
- 1
-

-
- ios
- masterpassword
-
(and 2 more)
Tagged with:
-
Hi I have recently read an article written by Tavis Ormandy, Link. So I'm curious to know that Enpass have these vulnerabilities or not?. Thanks
-
Good idea for future new feature, if will be exist in Enpass App for adding 2FA not one option but two options. Add 2FA - First option, scan QR Code Add 2FA - Or second add 2FA into Enpass via Security Code (some apps or websites not create QR Code but provide only Security Code) EDIT: Sorry guys :-D Now I looked, and Enpass is ready for this .. oh my eyes I maybe need glasses
-
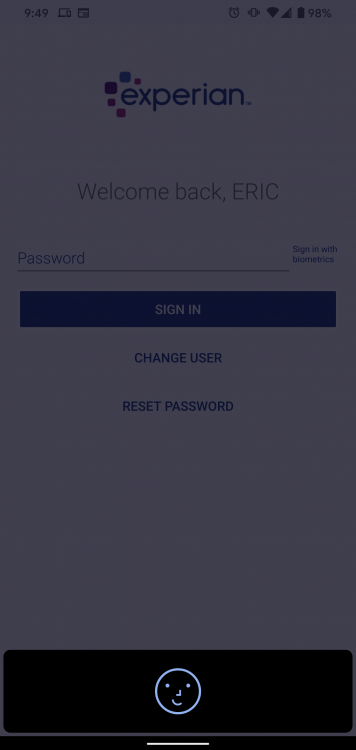
There are two ways to code Face ID on Android. One that requires you to press the confirm button after the face recognition process and one that doesn't. The extra confirm button press doesn't add any additional security. I wish Enpass would switch to the one that just unlocked when it saw your face. I have uploaded an example of the Experian app that used the one that doesn't require a confirm button press.
-
Hi there, Just a simple request: That Enpass has the ability to generate custom keyfiles. By default, Enpass estimates certain policies for its generation (128-bit or 256-bit), and as an option, it can be of almost any type of file extension (which is not so obvious, for advanced users). Even if it may be possible to use images with hidden text (steganography), either generated within the same Enpass or by third-party software. Understanding that steganography does not encrypt content, but as a way to hide already encrypted content in an image. KeePass (and clones) allow you to use custom keyfiles (almost any file), and I understand that it is authenticated by the "hash" of it (if it differs from when the keyfile originated or was associated, it simply discards it). What do you think about it, will it be possible to see something like this in the future? Gabe.
-
After using 1Password for a long time, I plan to go back to Enpass, the first password manager I used. This is mainly because multiple vaults are available in the latest Enpass versions. My 1Password account is secured with a master password, secret key and 2FA. At Enpass I will have to use a keyfile to make the vault just as safe. But where can I store my keyfile the best and easiest so that I can access it on any device (Windows, Android smartphone, Chromebook)?
-
I've been using Enpass for a while now and i'm well satisfied as my first password manager. An aspect that concern me the the most though, is the lack of protection aganist a master password sniffing attack or leak. Basically, as i understand, if you have the master password you can decrypt the database and take all the passwords, easy, without a second factor authenticantion or somenthing similar to stop it. And since you need to manually insert the master password everytime you want to unlock Enpass, this make the job easy for a keylogger, a zero day virus, or even a random security camera watching the screen of your smarthphone. Even if you have enabled the PIN option, you still need to insert the master password at least once a day. To remedy this, many password managers such as 1Password uses a secondary password called Secret password created locally by the password manager itself that you never need to type. I don't really know how it works since i never used it, but i got a similar idea: It would be possible to use the PIN to only unlock Enpass (the application itself), and leave the master password to crypt the database? So, even if the PIN get sniffed, it could be used only on that same device / Enpass instance. By letting only Enpass itself handle the master password internally. It's only a concept obviously, but it would be nice to a have an extra layer of protection. Also, i noticed that the auto-fill uses by default the "username" and "password" fields to fill all the login screens, even those who ask you for your "email" and "password". It would be also nice if you could choose what field use to auto-fill the request data, or make Enpass automatically recognizes which field to use by reading the web page or app window.
-
In the security settings it is clearly stated, that when using biometrics the master password has to be entered after a restart. However, after I restart my android phone I am still able to login with just my fingerprint. In my opinion either the description or the behaviour has to be updated. Better would be the behaviour since the password is currently stored somewhere on the device.
-
The less information that I need to provide, the more privacy, the more secure. I don't like that I need to register with an email address. (especially for the free/lite version.) Thank you.
-
I've recently installed Ubuntu 19.04 on my laptop with UEFI/SecureBoot and disk encryption enabled. when i tried to restore my vault from my cloud drive, it doesn't accept my masterpassword. after some research I found this: Is there an option to restore the vault with while keeping my disk encrypted? Like to see your thoughts.
-
I ran across an interesting article about some other well-known password managers out there, like 1Password, KeePass, DashLane & LastPass. https://www.securityevaluators.com/casestudies/password-manager-hacking/ If that's too technical, read ZDNet's summary on this article: https://www.zdnet.com/article/critical-vulnerabilities-uncovered-in-popular-password-managers/ While I was pleased Enpass wasn't on the list, I suspect it might be due to lack of significant market share like some of the other products. But I'm also very curious about the steps Enpass is taking to have independent third-parties pen-test the product. EDIT: I should have looked harder as Enpass has been audited in November of 2018! Audit results: https://dl.enpass.io/docs/EnpassSecurityAssessmentReport.pdf Security-related documents: https://www.enpass.io/?s=security&post_type=kbe_knowledgebase Please do not misconstrue what's being said here! I moved to Enpass several years ago, from KeePass which is mentioned in the article, and I am still very pleased with Enpass. So pleased that I have purchased it for family members and and strongly urged friends & coworkers who do not have a password manager to give Enpass a shot. The number one issue I hear about these other services is where that data is stored, and Enpass provides a great solution for data management since it builds on other well-known, and mostly trusted, storage products like Google Drive, OneDrive, DropBox etc. In any event, kudos to the Enpass team for the fantastic work they've been doing over the years, especially on v6.x. It's fantastic and I'm excited about what's next!
-
Hello, I have a suggestion for Enpass that increases the security of passwords and alerts the user when a website was hacked and a password change is recommended. The password manager 1Password has a feature called watchtower. They have an internal database of security breaches (database with information about hacked websites where user-data was stolen). In this database they store the website and also the date of the breach. 1Password stores for password entries two modification dates: modification date of the password modification date of the entry 1Password checks the password entries against this database. When a website was hacked after the password was changed in 1Password, then 1Password recommends to change the password. When the password was changed after the hack of the website, then users get no notification. So when the entry for a page was last changed today (like added some notes), but the password itself was changed 2 years ago, then users get a warning when the website was hacked 2 weeks ago. For the password manager KeePass there is a plugin available called HaveIBeenPwned. The plugin and the source code are available here: https://github.com/andrew-schofield/keepass2-haveibeenpwned This plugin downloads the public breach lists form "'have i been pwned?" and from "Cloudbleed Checker". The plugin checks (on demand) your passwords against these lists. In KeePass there is no modification date of the password. To get the modification date of the password the plugin checks the history of each entry and compares the passwords (to find out the modification date of the password). Suggestion: Please add also such a feature in Enpass in the Password Audits. In my opinion it is OK if you use the public available lists from "'have i been pwned?" and from "Cloudbleed Checker" (like the KeePass Plugin). This requires that you also store the "password modification date". When you import entries from KeePass then you should also determine the password modification date of the entry. In the KeePass XML the complete history is also exported. Regards OLLI
-
Hello, KeePass offers in the options the feature "Enter master key on secure desktop". When this option is checked then the dialog for entering the master password is shown on a secure desktop. This should prevent keyloggers from stealing the master password. Details about this feature you get here: https://keepass.info/help/kb/sec_desk.html If you want to see a screen shot of this feature, just google for "KeePass Secure Desktop" and you will find screen shots like this: (Source: https://img.raymond.cc/blog/wp-content/uploads/2016/02/secure-desktop.png) It would make Enpass more secure if you also use the Secure Desktop when entering the maser password or the PIN to unlock Enpass. This protects Enpass so the master password can not be stolen. I know that it is mostly the users fault if there is a keylogger on the system but it would be really helpful if Enpass is protected against keyloggers. Best regards OLLI
-
I talked with a colleague about password managers and he suggested 1Password. On the website of 1Password I saw on the "Tour" site (https://1password.com/tour/) some features of 1Password. One feature is very interesting and increasing the security: They show which sites in your vault support TOTP but the user has not set up TOTP. Here is a screenshot from the 1Password site: Suggestion In Enpass add the entry "Missing TOTP" in the section "Password Audit". Here you should show all password entries, where TOTP is possible but not set up by the user. Here is a list of services that support TOTP: https://twofactorauth.org/ We had a Doxxing scandal in Germany where a young guy published many private information stolen from accounts of German politicians and German celebrities. This guy was able to steal the data because the accounts used very weak passwords (like 123456) and were not secured with TOTP. So this feature increases the security a lot!
-
Dear Developer, Enpass is very good app but i miss some features like device administrator. For protecting app from uninstalling via other unauthorized persons.. or accidentally uninstalling... Also add fevicon as soon as possible. And add full UI change log in new updates description in google play so we can check on which area you modify UI.
- 1 reply
-
- beta
- feature request
-
(and 2 more)
Tagged with:
-
Hello, I read in a computer magazine that there is a new Browser Extension for Google Chrome called Password Checkup https://chrome.google.com/webstore/detail/password-checkup/pncabnpcffmalkkjpajodfhijclecjno When I sign into websites this extensions checks if the password that I have entered is pwned . Then a message box is shown telling me if the password was pwned (message box is red) or if my password is still safe (message box is green). I think it would be useful when Enpass also checks passwords at login. But you should only show a message when the password was pwned. Best regards OLLI
-
Hello, I have a suggestion for Enpass that increases the security of passwords and alerts the user when a website was hacked and a password change is recommended. The password manager 1Password has a feature called watchtower. They have a internal database of security breaches (the site was hacked and user data was stolen) and check if the password of the specified website was changed after the breach. So they have two modification dates: one modification date of the password itself and one for the total entry. Example: The password entry for a page was last changed today, but the password itself was changed 2 years ago. When there was a breach for this website 6 months ago, then 1Password would alert the user and recommend a password change. For the password manager KeePass there was a new plugin released today, called HaveIBeenPwned. This plugin downloads the public breach lists form "'have i been pwned?" and from "Cloudbleed Checker" The website of the plugin is https://github.com/andrew-schofield/keepass2-haveibeenpwned Suggestion: I suggest that you add also such a feature in Enpass. In my opinion it is OK if you use the public lists (like the KeePass Plugin). So Add in the "Password Audit" two new entries for these services and check all password entries. It is up to you if you implement a separate modification date of the password. Regards OLLI
.thumb.png.18d5ca31a9a3b5e1b86913420f39b434.png)